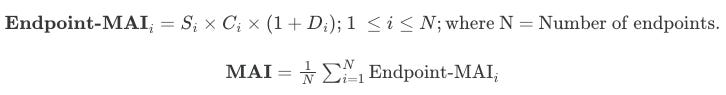Governing MCP Risk: Board-Level Controls, KPIs and Operationalising Trust (Part-3)
How executives translate technical MCP defences into boardroom assurances, measurable KPIs and procurement guardrails.
Parts 1 and 2 explained why MCP creates new attack surfaces and gave a practical engineering playbook (gateway, sanitisers, provenance, tool manifests, output filters). Now we elevate the conversation: how to govern MCP risk so that CISO, CTO and product leadership can measure, budget and accept/reject MCP-enabled features.
The Executive Problem Statement:
MCP is attractive because it reduces integration cost and accelerates product features. But it also moves sensitive decision-making to an automated layer that can reach across systems. That means senior leadership must treat MCP deployment as a risk decision - like adopting a new identity provider or outsourcing a database - not merely a dev feature.
NIST’s AI RMF and OWASP’s LLM Top 10 both call for governance, monitoring and periodic red-teaming across the AI lifecycle.
Introducing the MCP Attack Surface Index (MAI):
The MAI is a single number that tells leadership “How exposed are we right now because of MCP?” It replaces the vague “we have some MCP servers” with a concrete, trending metric that correlates directly to risk and budget.
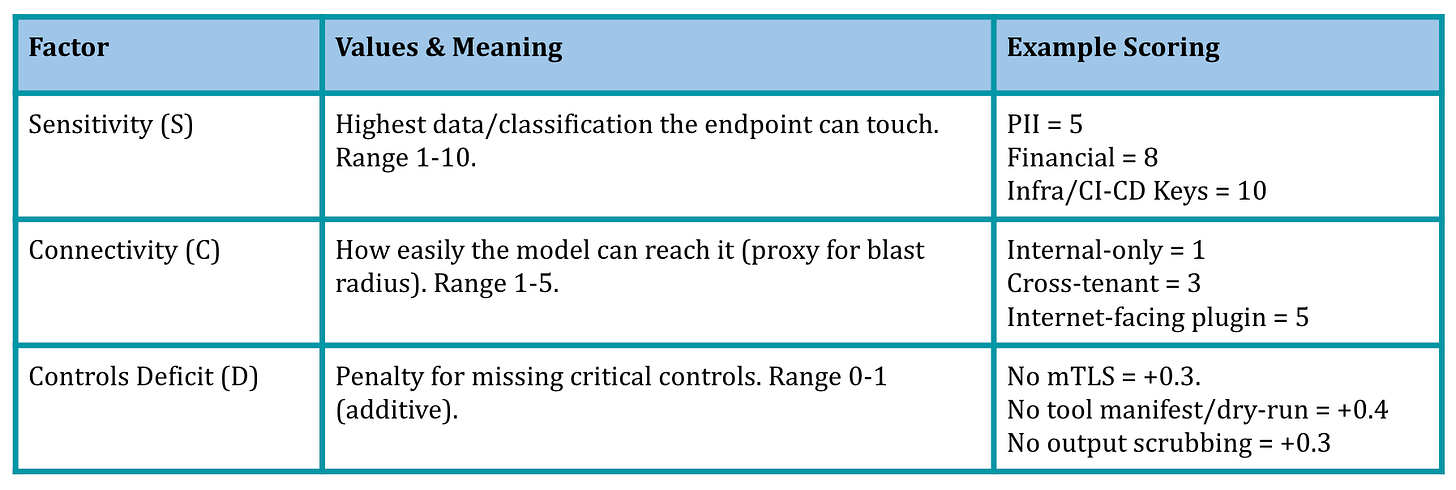
For each MCP Server Endpoint we define following 3 configurable knobs:
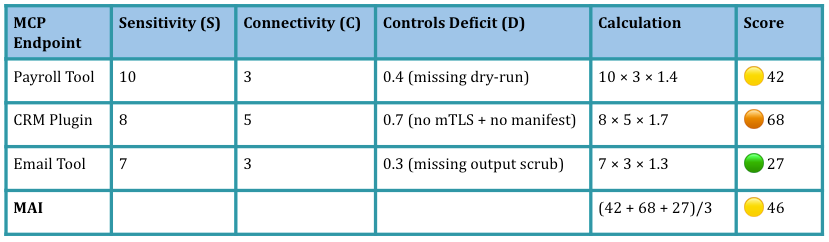
For illustration; following are few ranges for a fully hardened endpoint i.e. with D ≃ 0:
Most internal tools: S = 6–8, C = 1–2 ⇒ Endpoint-MAI = 6–16.
High-value tools (CRM, payroll): S = 8–10, C = 2–3 ⇒ Endpoint-MAI = 16–30.
Internet-facing plugins: S = 8–10, C = 4–5 ⇒ Endpoint-MAI = 32–50.
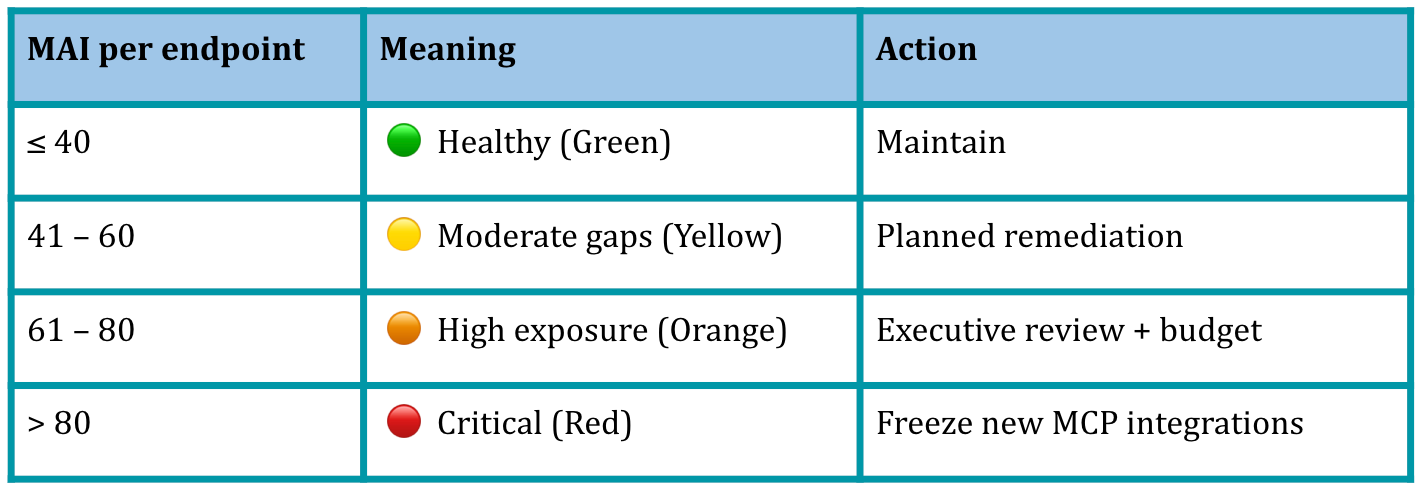
An LLMOps observability product’s dashboard can show the single MAI metric as well as flag any contributing individual Endpoint-MAIs which are > 40.
Example:
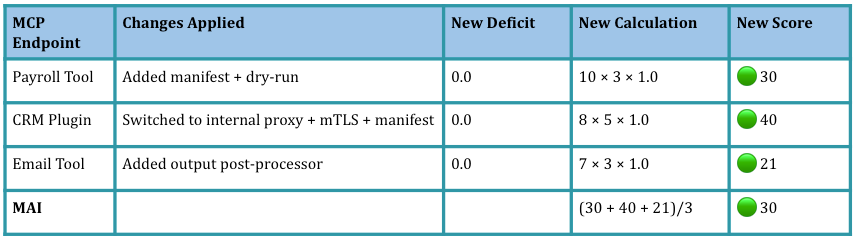
After applying Part-2 hardening playbook; there is a 35% reduction in MAI:
Board-Level Controls & Deliverables:
MCP Risk Register:
Maintain a prioritised register of MCP-exposed assets (which corpora, tools and tenants are connected), exposure level, mitigation status and owner.
Update monthly and surface to the security committee.
MCP Acceptance Criteria for Product Releases:
Any new feature that wires MCP to internal systems must pass a checklist:
Limited Scope
Ingestion Gates
Tool Manifests
Output Filters
Incident Playbook
Connected SIEM Logging.
Key Metrics for Exec Dashboards (Operationalised Weekly):
MCP Attack Surface Index (MAI): The overall MAI as well as per Endpoint-MAI; as explained above.
MCP Policy Compliance Rate: % of MCP calls that passed deterministic policy checks.
MCP Incident Mean Time To Detect/Respond (MTTD/MTTR): Tracked in minutes/hours.
ARI (AI Reliability Index) Integration: Include MCP-related correctness & cost predictability sub-metrics (ARI framework from FortifyRoot research, inspired by NIST metrics).
Budget & Insurance:
Budget for continuous red-teaming and MCP testing as an operational line item. Insure critical data-flows and vendor risks where feasible.
Policy & Procurement Controls:
Vendor Security Baseline: Require MCP providers or plugins to demonstrate mTLS support, signed manifests, audit-logging and SBOMs for tooling.
Least-Privilege Contractual Clauses: Vendors must accept a bounded scope of access and provide emergency kill-switches.
SLA + Forensics: Vendor SLAs must include forensics support and timeline for data exposure notification.
These steps align with supply-chain risk management principles in the NIST AI RMF and OWASP guidance.
Operational Governance - People and Process:
MCP Owner & Escalation Path:
Assign a single MCP Owner (platform/security engineer) with clear SLAs for onboarding/approvals.
Emergency path: Revoke MCP server certs, block MCP domain in gateway.
Quarterly Red-Team & Tabletop Drills:
Run simulated MCP poisoning and exfiltration drills every quarter. Use MITRE ATLAS scenarios and OWASP attack patterns to script tests.
Audit & Evidence:
Capture immutable audit trails: ingestion logs, retrieval decisions, tool calls and output post-processor decisions. Preserve for regulatory or forensics needs (retain per policy).
When to Say “No” - Risk Tolerance & Thresholds:
If a proposed MCP integration touches regulated personal data (PHI, financials) and the vendor cannot prove end-to-end encryption + audit logs, decline.
If a feature cannot be scoped to a single curated corpus, delay until ingestion hygiene and down-ranking are in place.
If the product requires side-effecting tools that operate outside a sandbox account, refuse until dry-run & reviewer controls exist.
Building Trust - Reporting to Boards & Customers:
Monthly MCP Health Snapshot for the board: MAI, policy compliance, incidents and red-team outcomes.
Customer Transparency: Publish data residency and MCP policies in the product’s security white-paper. Provide customers the option to disable external MCP endpoints for their tenant.
Third-Party Audits: Annual independent review of MCP controls to support SOC2 / enterprise procurement.
Conclusion - Governance as a Multiplier:
MCP is not an optional bolt-on; it changes the threat model and the governance model. Technical controls from Part-2 are necessary, but insufficient without executive ownership: KPIs, budgeting for red-teaming, procurement clauses and clear “no” conditions. Organisations that treat MCP as infrastructure - with policy, SLAs and auditability will gain the feature advantage with managed risk.
Further Reading:
We’re FortifyRoot - the LLM Cost, Safety & Audit Control Layer for Production GenAI.
If you’re facing unpredictable LLM spend, safety risks or need auditability across GenAI workloads - we’d be glad to help.